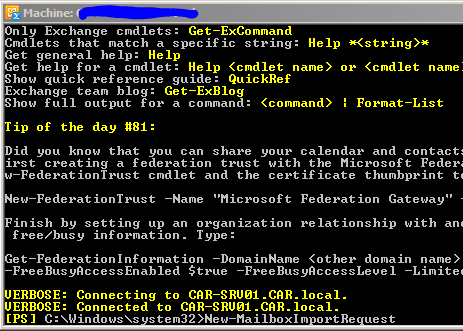
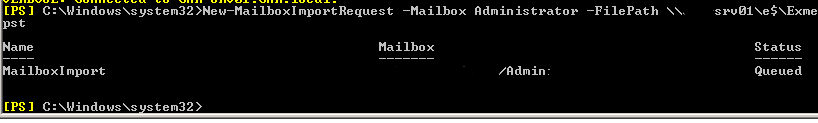
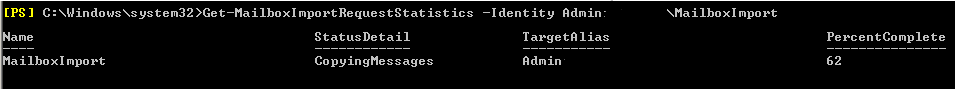
Storage Pools are a new feature in Windows Server 2012 that at first glance (at the terminology) may look like software RAID arrays that have been around for years, but are really a new concept, or at least several generations of advancement on the old concept. They give us the ability to use disks of different sizes and bus types and create a single ‘pooled disk.’
While Storage Pools are easy to create and use, the technology under the hood is quite complex, and certainly years ahead of anything we had seen before. Storage Pools leverage the power of virtual hard disks and ‘thin provisioning in order to deliver ‘on demand’ storage.
Let’s create a scenario in which we see the true value of Storage Pools:
Someone in your organization is working on a virtual server that will start small but will necessarily grow over time. They request 185GB of storage for their VM. Because of the importance of the project they request the fastest solid-state drives (SSDs) available. You have one 64GB drive available immediately, but the part is on backorder and will take several weeks to get in.
Rather than simply installing the disk into a server and provisioning the VM onto that disk, you connect it, create a Storage Pool, and add the disk. You then create a virtual disk on the Storage Pool, and then create a volume on that pool. You should now have a volume of about 63GB (formatted capacity) ready to allocate to the VM. The project proceeds.
A few weeks later you receive your new SSDs, and not a minute too soon because the VM is growing. You install the new disks into the server, and from the Storage Pools screen in Server Manager you add the new drives to the pool, expand the virtual disk, and then extend the volume. Within minutes you have the 200GB volume (on SSDs) that was requested.
Let’s extend beyond the single server though. You may need an iSCSI SAN, but do not have the budget for it. Rather than make do without, you take a NAS (Network-Attached Storage) or JBOD (Just a Bunch Of Disks) appliance which are both much less expensive, and create your Storage Pool using those disks. Then from within Windows Server 2012 you use the iSCSI Software Target to start creating LUNs on the appliance, thus creating the SAN device you couldn’t afford.
The hardware
I will preface this by saying that for servers I always strongly recommend server-grade hardware. However sometimes we do not have the budget for the best hardware, and we have to use what is available. Storage Spaces are supported on any type of drive you can connect to your computer, be it SATA or IDE, SCSI or SAS, iSCSI, or USB. With that being said, if you are going to use your Storage Space for failover, only SAS and iSCSI are supported by Microsoft. However it is even possible to create a Storage Pool of USB keys, as long as they are connected to your computer.
Creating your Storage Pool
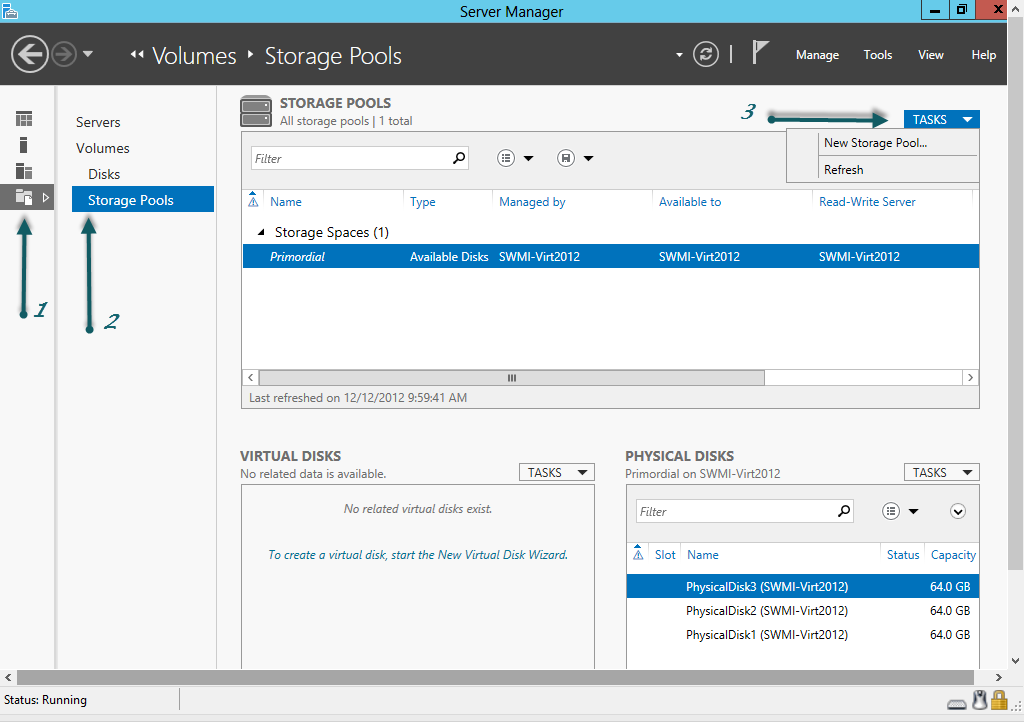
- From within Server Manager click on the File and Storage Services workspace.
- In the navigation pane select the Storage Pools context.
- To the top-right of the Storage Pools workspace click on the TASKS drop-down and click New Storage Pool…
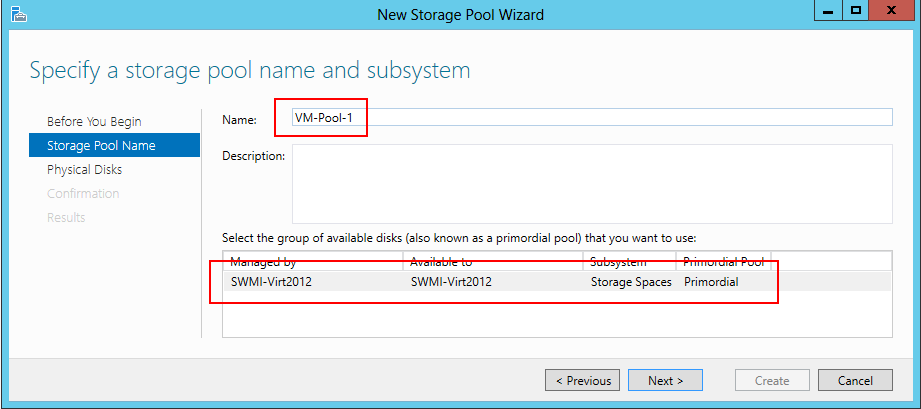
- In the Specify a storage pool name and subsystem window name your pool, and select the group of available disks that you will use and click Next.
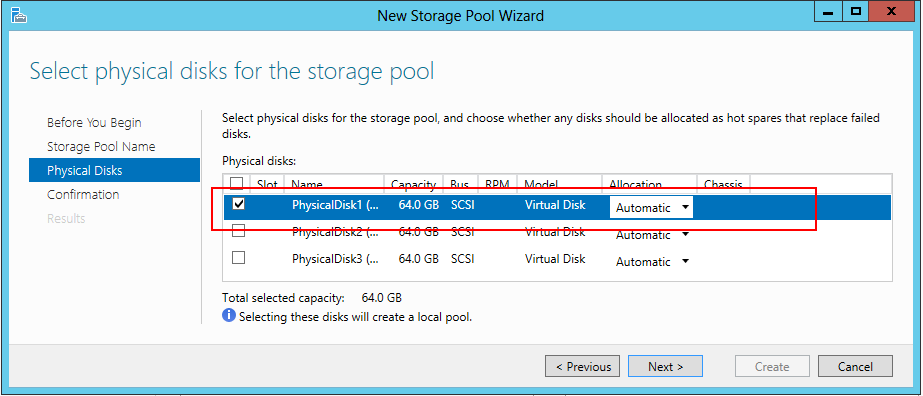
5. Select the physical (or in this case virtual) disks that you would like to add to your pool and click Next.
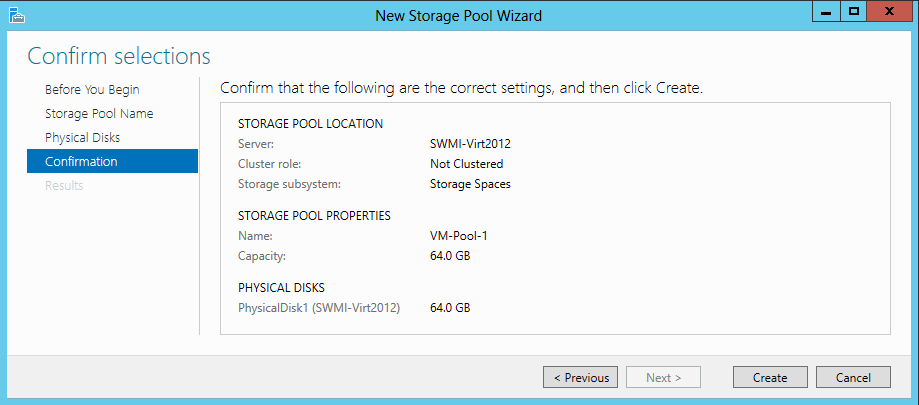
6. On the Confirm selections page click Create.
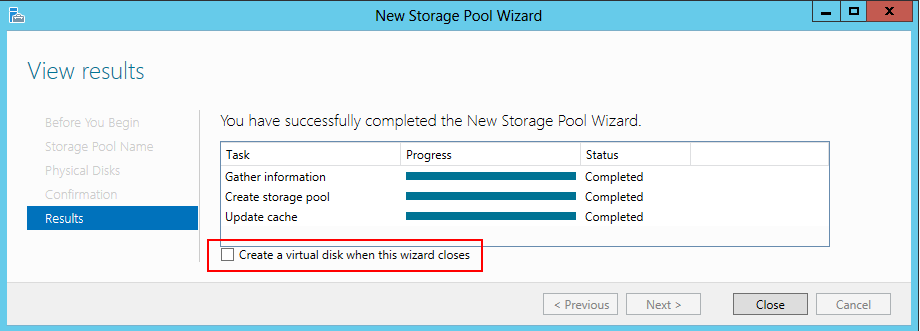
It will not take very long, and you will get a message that you have successfully created a Storage Pool. Before you close the dialogue box, notice that near the bottom there is a checkbox asking if you want to create a virtual disk when the wizard closes. Select this checkbox and then click Close. The New Virtual Disk Wizard will come up automatically.
7. In the New Virtual Disk Wizard select your newly created Storage Pool onto which to create the virtual disk, and then name the disk as you would.
8. In the Select the storage layout screen you are asked to select between Simple, Mirror, or Parity.
Simple: data is striped across the disks, maximizing the capacity and increasing throughput, but without offering any redundancy thus decreasing reliability. You are not protected from disk failures.
Mirror: data is duplicated on two (or three) disks which increases reliability, but reduces capacity. A mirror requires at least two disks to protect from a single failure, and five disks to protect from two simultaneous disk failures.
Parity: data and parity information are striped across the disks, increasing reliability but reducing capacity. It requires at least three disks, and cannot be used in a failover cluster.
9. In the Specify provisioning type screen you can choose either thin-provisioned (your virtual disk starts small and grows as needed) or fixed-provisioned (your virtual disk is created as the fully provisioned file).
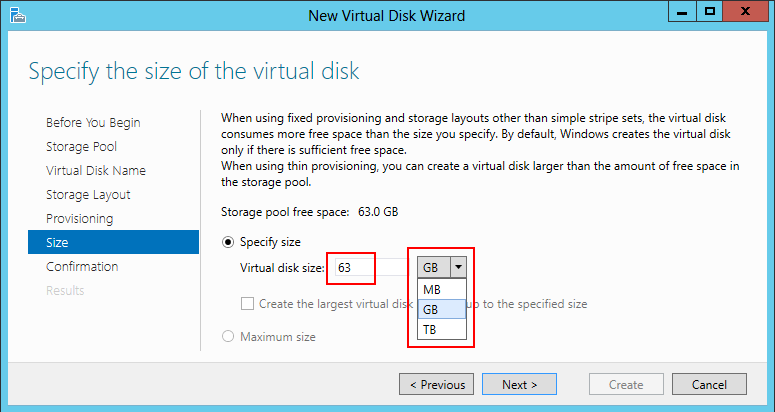
10. In the Specify the size of the virtual disk page enter the size of disk, and from the drop-down list select the unit of measurement – megabytes, gigabytes, or terabytes. Click Next.
On the Confirm selections screen verify that your settings are right and click Create. This process should not take very long.
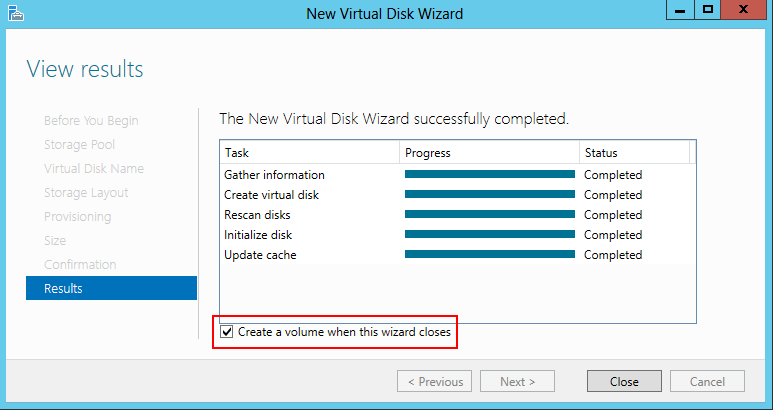
Once again, at the bottom of the View results page we have a checkbox, this time asking if we want to create a volume. Leaving this checked will bring up the New Volume Wizard.
The wizard will look a little different than it did in Server 2008, owing to the fact that you can now provision storage both locally and remotely. On the first screen you select the server and the disk; on the second screen you select the volume size (which cannot exceed the size of the disk); you then assign a drive letter or, if you prefer, a directory to mount it to (or don’t assign a letter at all); finally you select the file system, unit size, and volume label. On the last screen you confirm your selections and click Create.
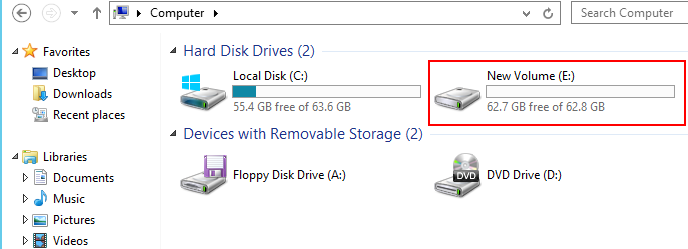
The volume will not take long to create, and you are now done. You can navigate to Computer in Windows Explorer and your newly provisioned drive is ready to use!
Growing your Storage Pool
Creating it is one thing, but let’s now see how easy it is to extend the volume by adding drives.
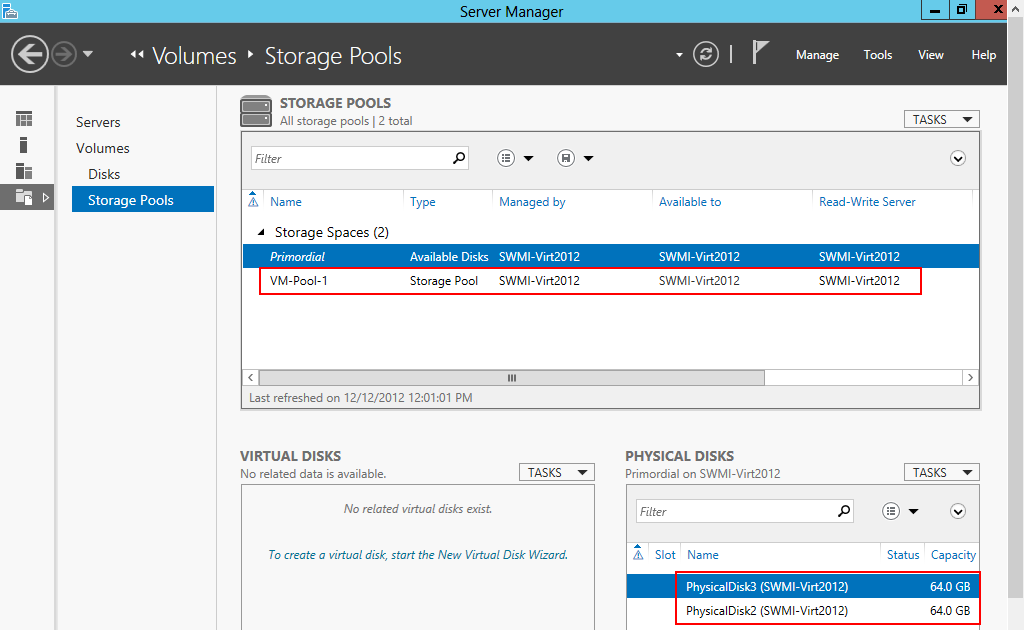
When we navigate back to our Storage Pools workspace in Server Manager we see that our newly created pool is there; we also see (under Physical Disks) that we have two 64 GB disks that are unused (thus primordial).
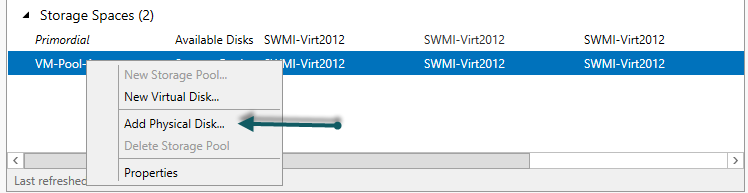
- Right-click on your storage pool and click Add Physical Disk…
- Your available disks will be listed. Select the ones you wish to add and click Next.
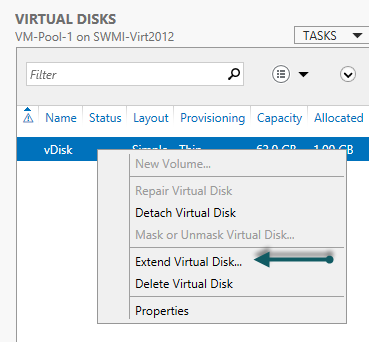
- In the VIRTUAL DISKS context on the Storage Pools workspace right-click on your virtual disk and click Extend Virtual Disk…
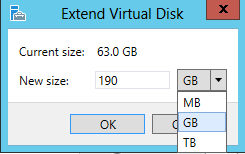
- In the Extend Virtual Disk window enter the desired new size and click OK.
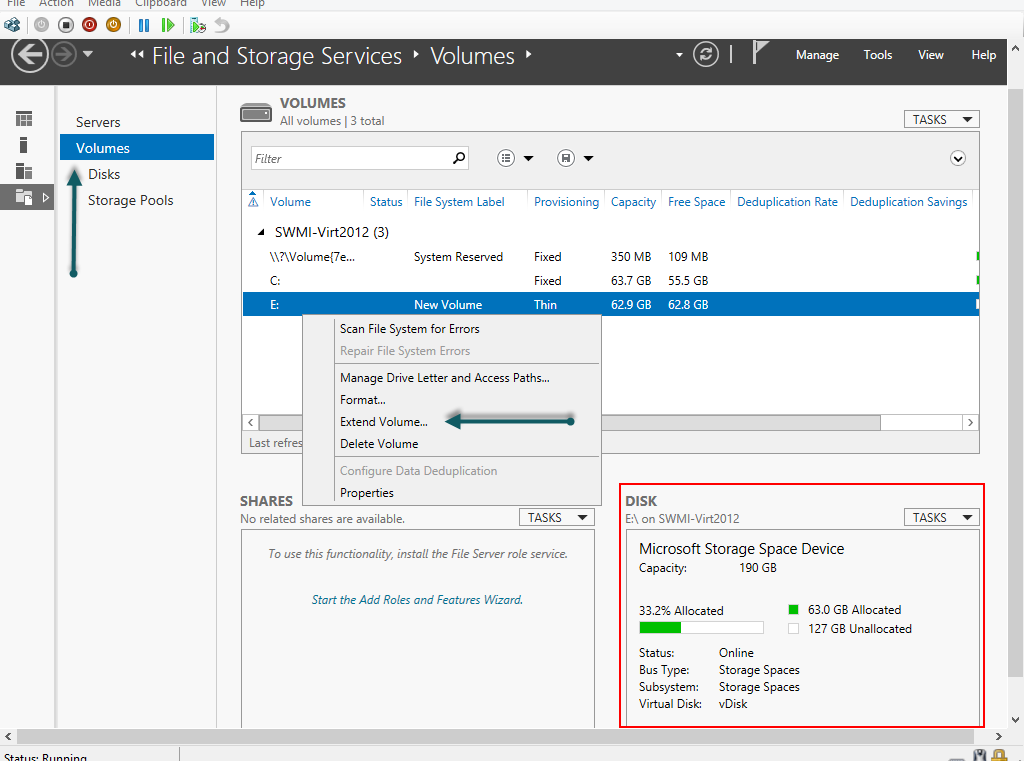
- Now you are going to change the context to the Volumes workspace. Right-click on the volume that you created and click Extend Volume. Notice when you click on the volume the Disk is listed as belonging to a Microsoft Storage Space Device. It lists the capacity, both allocated and unallocated, as well as the status and virtual disk name.
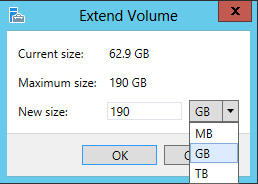
- The Extend Volume window looks identical to the Extend Virtual Disk window. Enter the new size and click OK.
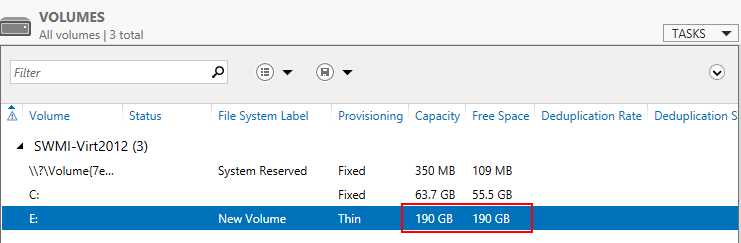
- Extending the volume only takes a few seconds, and when you are done you will see that the capacity has been extended.
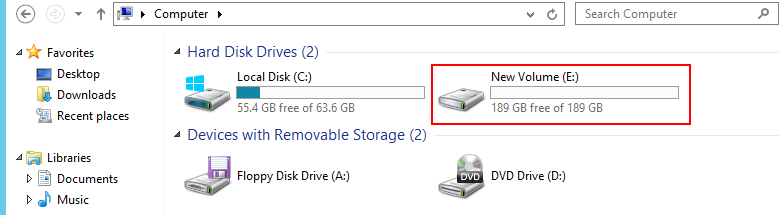
If you want to double-check, go to Windows Explorer and navigate to Computer in Windows Explorer and (once you hit refresh) your newly extended drive is ready to use!
Conclusion
Storage Spaces are going to revolutionize the way we (as administrators) think about storage. We can now hot-add drives to volumes and extend them in seconds and not hours, and because there is no downtime involved we will not have to do any of this after hours.
Going forward we are going to stop thinking about the disk as the main storage unit of storage in our environment, but rather it will be one piece of the equation. Our volume sizes will not be limited to the size of a disk, but what we need, whether that be measured in gigabytes or terabytes.
Add to the fact that we are not tied to any specific architecture, and you will see very quickly that our storage costs and complexity will drop – even as we add features like mirroring, failover disks, and parity.