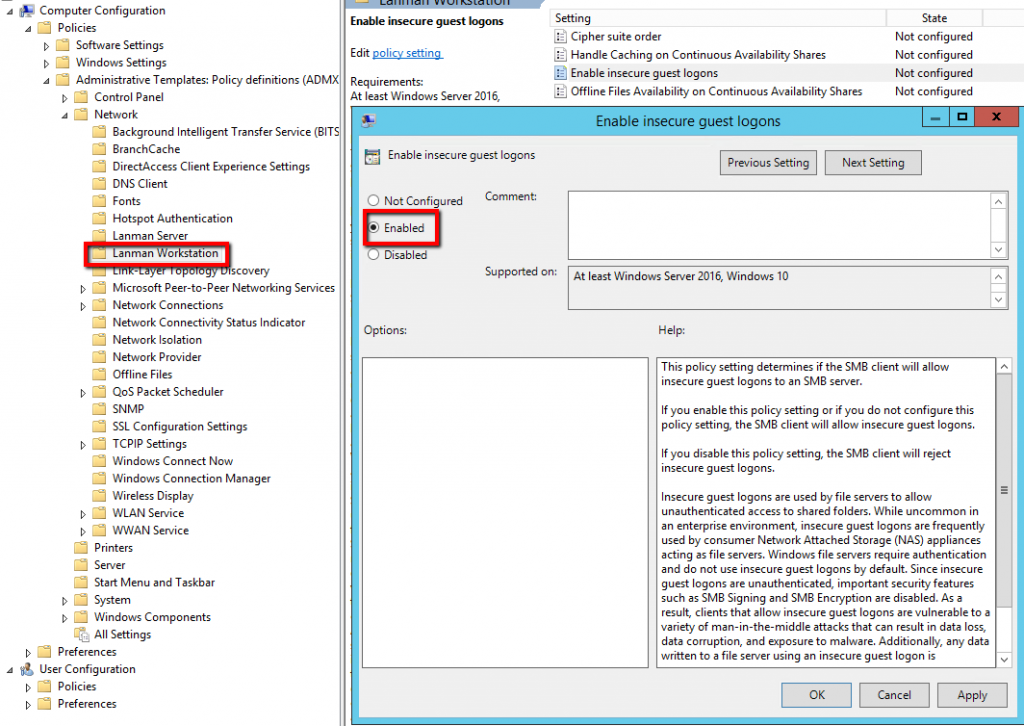
When you home lab and you don’t have Microsoft license for RDS, you have two options. Reinstall the server (redeploy the VM) or cheat a bit. Yes, in fact, there is cool hack which allows you to reset the 120 day grace period on Windows Server 2012 R2 RDS, and we’ll show you how. I like doing posts which shows some cool hacks, and this is exactly this kind of post – How To Reset 120 Day RDS Grace Period on 2012 R2 Server.
Normally you would need to activate the RDS/TS CAL License server and point the Server to License server with User/Device License and will resolve the problem. However, we don’t want to do that because we have no license from Microsoft, in our lab. (and many other IT pros who test stuff in the lab too).
What we will do is simply reset the default timer which is 120 days grace time, when you first add the RDS role. In fact, you do not need to reboot the server either. Simply log out and back in and the message changes from let’s say 54 days left to 120 days left. And that’s it.
Note: This tip works also on Windows Server 2016 and Windows server 2019
For every admin who runs homelab or has a cloud lab, this is a must known hack.
Step 1: Connect to your RDS Server as an admin and open regedit.
Navigate to the following key:
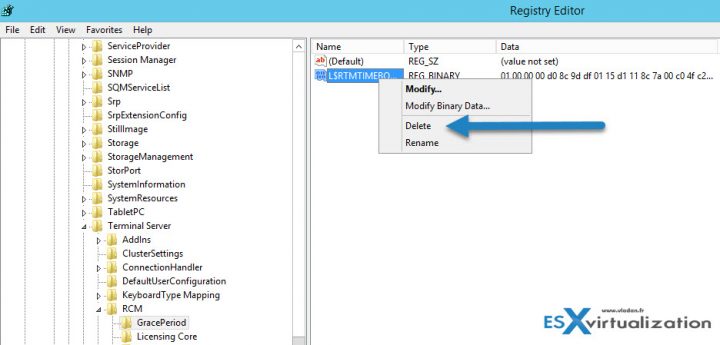
The solution is to delete the REG_BINARY in:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerRCMGracePeriod
It’s called a “TimeBomb” … -:)
Note: You must first take an ownership and give admins the full rights.
Like this:
Go to menu Edit > Permissions
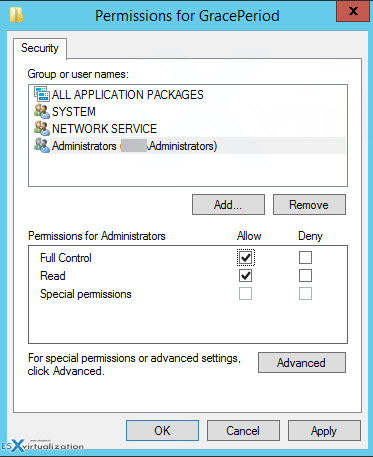
Once you delete the Registry key you must reboot the host. Some users have reported that when not rebooting the host you will see the message changing, but no connections are possible.
Update: Well, in fact, you can just restart the Service “Remote Desktop Services” which will momentarily disconnect all the active sessions and then after a minute or so you can reconnect to the sessions.
You should see the message changing at the taskbar area….
Note that you have also a possibility to check how many days its left… Go to the command prompt and enter this command (not tested).
wmic /namespace:\rootCIMV2TerminalServices PATH Win32_TerminalServiceSetting WHERE (__CLASS !=””) CALL GetGracePeriodDays
Apparently, you can delete this key every time it expires ….. indefinitely. Wow. That’s good to know too.
This is it my friends. Today’s tip for home labs.
Second Tip:
Download a PowerShell script from Microsoft allowing you to reset the RDS grace period. Mirror here: Reset-TSGracePeriod.ps1
Quote from Microsoft Technet:
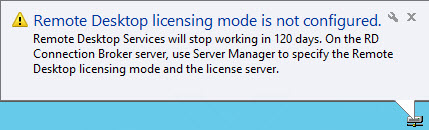
The PowerShell script can be used to query and reset terminal server grace period to default 120 days if it is nearing to the end. We often need to deploy Terminal Server (Remote Desktop Session Host in 2012) for testing purposes in development environments allowing more than 2 concurrent Remote Desktop Sessions on it. When it is installed, by default if no RDS or TS Licensing server is specified via either GPO or Registry, it is in default Grace period which is 120 days and it works fine until then.
Once Grace period expires, the server does not allow even a single Remote Desktop session via RDP and all we are left with is to logon to the Console of machine using Physical/Virtual console depending on Physical or Virtual machines or try to get in using mstsc /admin or mstsc /console, then remove the role completely and restart the terminal server (RDS Server) and post that it starts accepting default two RDP sessions.