The ability to convert existing Physical hosts to Virtual machines is often the biggest return on investment benefit to justify the case for virtualisation. Taking a legacy platform often on older, unsupported hardware and software, and converting it to a virtual machine running with many other machines, but on new, high capacity hardware taking up less space and power is a key driver for virtualisation.
Older systems consuming a relatively high amount of energy and space for what is now very low processing power, can be converted to VM’s hosted on much more powerful hardware for a similar footprint but with much increased agility through the well understood benefits of virtualisation.
A recent project The Full Circle (www.thefullcircle.com) undertook as part of our private cloud practise, was to rationalise several older HP ProLiant DL360 servers (one had a BIOS dated 08/03/2001 – over 10 years old!) each taking 1U of rack space, some with dual power supplies, dual network adaptors, mirrored disks, etc. all generating high heat output (which in turn has high cooling costs).
Online Windows server capture using Sysinternals Disk2vhd utility
If you haven’t got Microsoft’s Virtual Machine Manager suite and you don’t want to spend many hours backing up the source server, creating a blank VM, installing a base O/S and then hoping a restore will work without hours of troubleshooting disparate hardware issues… really?!?! there is a handy alternative from those clever folks at Sysinternals – disk2vhd.
From Sysinternals “Disk2vhd is a utility that creates VHD (Virtual Hard Disk – Microsoft’s Virtual Machine disk format) versions of physical disks for use in Microsoft Virtual PC or Microsoft Hyper-V virtual machines (VMs). The difference between Disk2vhd and other physical-to-virtual tools is that you can run Disk2vhd on a system that’s online. Disk2vhd uses Windows’ Volume Snapshot capability, introduced in Windows XP, to create consistent point-in-time snapshots of the volumes you want to include in a conversion.”
Overall P2V process as easy as 1,2,3…
Of course it’s not as easy as 1,2,3… this process may take from only a couple of hours to a couple of days per server but its a straightforward process with no fundamental ‘gotchas’ – although in-between application licensing, network infrastructure issues, and later VM contention (disable those traditional backup agents!) – this part may prove to be the simplest part of the process, which is:
- Capture of source physical host/server
- Audit hardware and software build
(recommend paid tools such as Belarc, but also include built-in such as systeminfo – knowing the local machine Administrator account rather than a domain account could be useful although not mandatory although you do need an admin account)
- Full Backup! (whilst no changes planned to source machine a backup maybe useful later)
- Clean-up the source machine (old profiles, programs, recovery points, temp files (could use CCleaner or just cleanmgr.exe), and always defrag! – great tip from Khwajakhurram in the comments))
- Disk conversion from physical source to Virtual Hard Disk file target (VHD)
- Build of Virtual Machine / VM hardware to be a near-as match to the source hardware in terms of major physical resources such as CPU, Memory, Disk, and Network
- Attach the created VHD file, note this will be one Disk that may contain multiple partitions (recommend capturing individual volumes to separate VHDs)
- Clean-up of new virtual machine hardware and system software
- Install the Hyper-V Integration Services (may have pre-reqs..) and restart
- remove superfluous hardware devices, drivers, and system software (may require several restarts)
- Setup networking (you will have lost the physical adapters)
- May wish to change storage properties e.g. converting from a Basic to Dynamic Disk in order to Shrink a volume, etc…
- Check the event logs for any errors to determine if serious or can be ignored
- Test, test, test!
- Activate Windows (the ‘hardware’ will have changed significantly)
Steps in more detail..
Running disk2vhd
You don’t even need to permanently install the tool on the source machine, simply browse to http://technet.microsoft.com/en-us/sysinternals/ee656415 and click ‘Run Disk2vhd’
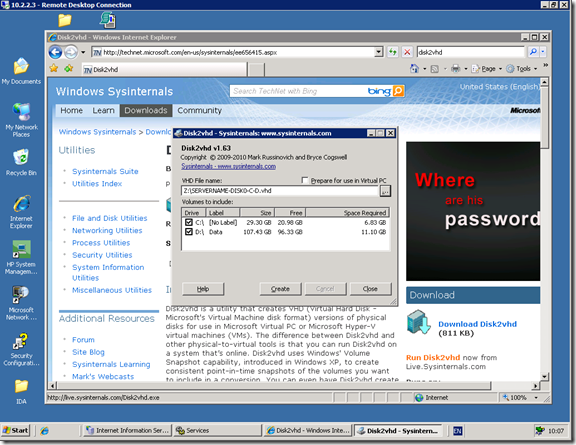
choose your source drives, enter a suitable target destination with sufficient space and click create – this may take some time (as in several hours depending on size, speed, network, etc.)
Setting up the captured hard disk
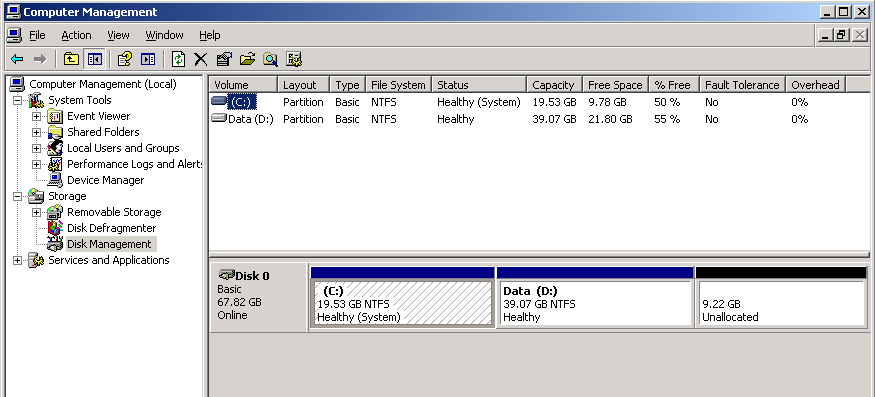
The disk captured by disk2vhd will be a single hard disk image of the selected partitions/volumes, this may be fine if they combine less than 127GB as the first Hyper-V bootable disk has to be attached to the IDE controller (with a disk limit of 127GB)
However, for production use we recommend splitting your disks in the virtual world as you would in the physical – capture each volume to a separate VHD e.g. HOSTNAME-diskN-c_system.vhd, HOSTNAME-diskN-d_data.vhd, etc.
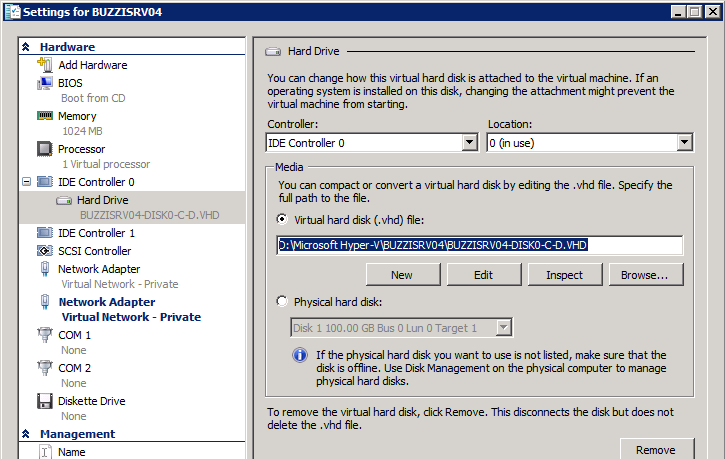
Here’s a grab of a SCSI based system which had 2x73GB SCSI disks as a single RAID disk
P2V for Windows Server 2003 onto Hyper-V
Windows Server 2003 machines require Service Pack 2 to be installed before the Hyper-V Integration Services can be installed – get ready to install using the keyboard as until the IS bits are installed you have no mouse!
Removing superfluous hardware devices, drivers, and system software
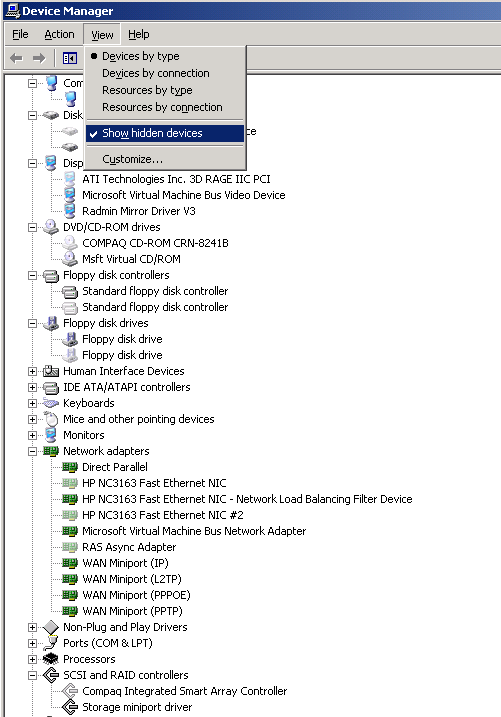
You need to get familiar with removing hidden devices and how to show non-present devices by following the Microsoft KB ‘Device Manager does not display devices that are not connected to the Windows XP-based computer’ basically:
set devmgr_show_nonpresent_devices=1
start devmgmt.msc
And then show hidden devices, to allow removal of the no longer supported devices, below shows the main areas to cover from a HP ProLiant server to VM:
I’m fairly confident to remove ALL hidden/greyed-out devices, especially if its a device that has been replaced by another ‘active’ / non-hidden instance of the same name e.g.
Note – this is a tedious process working through all greyed-out devices – suggest using the keyboard to save time (cursor to device, delete, enter, use of home & end keys, then repeat – many times! 😉
If you delete something in error don’t worry – you can always re-scan for hardware changes or restart the machine – you’ll be doing a few restarts during the process anyway…
Some things should be removed that are not hidden
Some devices won’t be hidden, but if you know your hardware and device drivers fairly well you should be able to spot the obvious candidates for removal, e.g. the Compaq Smart Array Controller drivers used for managing the hardware disk array.. cpqarry2 is definitely one to go..
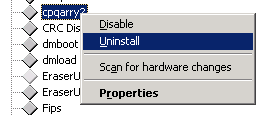
but most will (be hidden), including related components…
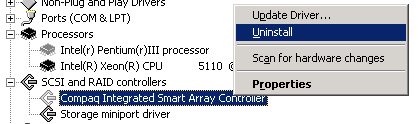
(I think the Pentium III chip can go in this case!  )
)
Note – some of these may prompt for a restart, I normally bank several restarts together, but some system software to be removed may require a restart to uninstall cleanly..
System software uninstallation and many restarts
Most server systems may also have significant software components to uninstall, in this case several HP components that talk to proprietary HP systems management components that will no longer be present in the virtualised machine.
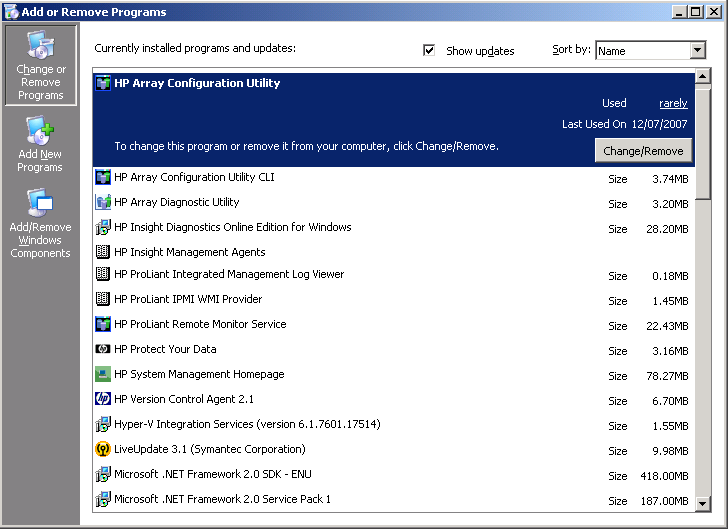
HP Network Teaming Utility – where is that software?
The HP Network Teaming Utility – easily spotted on most HP Windows server systems by the  logo in the system-tray, however the software is not that easily found as doesn’t appear in Add/Remove Programs nor is removed from Device Manager.
logo in the system-tray, however the software is not that easily found as doesn’t appear in Add/Remove Programs nor is removed from Device Manager.
Open network connections (ncpa.cpl) and select the ‘HP Network Configuration Utility’ then select Uninstall – you should be prompted to uninstall per:
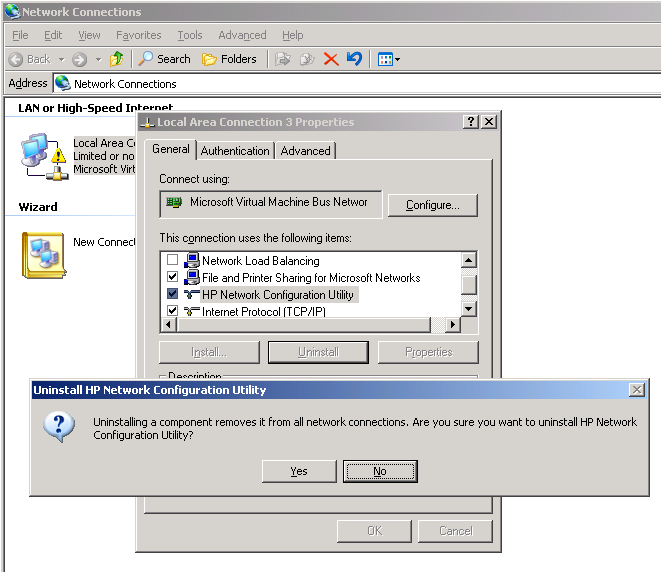
You’ll be prompted for a restart, and by now the system probably deserves one!
Recreate your Network connections
Its time to dig out that systeminfo report, as that’s going to have a concise listing of the source server’s network settings in terms of IP addresses, etc. – if you’re converting from large-frame/iSCSI with VLANs etc. then that scenario is slightly beyond the scope of this post – sorry, but some things have to be billable!
Errors on start-up?
You are bound to get some start-up errors at the end of the process, although hopefully these should be insignificant such as a w32tm service unable to update from NTP or a domain controller due to network changes (e.g. still testing on a private network). You may also have dependency components that still require removal such as a System Management Controller via the Service Control Manager (typical event id 7000 stuff).
Fire up the Event Viewer (eventvwr) regardless and have a trawl through the event logs, even if you didn’t get a error starting service alert on start-up you may find issues that require further investigation – effort here will be worthwhile for a stable and error free machine.
At the end of the process…
When you’re finished, sit back crack open a can (if you won’t get caught with food and drink in the data center) and have a think what nice new tin you’ll replace all those gaps in the rack with… mine would be Stella…  Better still, for you, the company and the planet, return a few racks to the data center manager / co-lo provider, and ask for a bonus from all the carbon you’ve saved
Better still, for you, the company and the planet, return a few racks to the data center manager / co-lo provider, and ask for a bonus from all the carbon you’ve saved